©2015 -



Information Technology



The Oracle Advanced Security Option (ASO) provides the foundation to meet the security requirements for compliance and regulations. This feature comes "built-
In particular, the PCI DSS compliance requirements basically evolves on the protection of the stored card holder data (encryption of Data-
This article are my guidelines to quickly setup a secure database by example from my own lab. It focuses on securing data in-
TABLE OF CONTENTS
Oracle Advanced Security Concepts
Benefits of Oracle Oracle Data Redaction
Network Communication Encryption
Oracle Advanced Security Configuration
Oracle Wallet And SSL Cert Setup
I. Create A Wallet on Server And Client
II. Create A Cert Request For Database Server
III. Create A Cert Request For Client Application
IV. Export Certificate Signing Request
Generate PRIVATE KEY for Root Trusted Cert
Generate TRUSTED ROOT CERTIFICATE
V. Import Trusted Root Cert Into The Wallet
VI. Import Signed Cert Into The Wallet
VII. Import Signed User Cert As Trusted Certificate
Secure Database Network Connections
How To Setup Secure Database Connections Using SSL
Configure The Database Server Oracle Net files
Configure The Client Oracle Net Files
How To Setup End-
ORACLE ADVANCED SECURITY CONCEPTS
Oracle Advanced Security is a licensable feature embedded on the database that provides additional functions to support Transparent Data Encryption (TDE), SSL network encryption, and on-
TDE stops would-
- Designed to protect data in storage (memory and files).
- Allows encryption at the table level (columns) or at tablespace level (datafiles).
- Supports file encryption of backups and data pump exports.
- Data remains encrypted at the database buffer cache, undo, redo buffer cache, and storage files.
- Transparent to users and applications by employing automatic encryption when writing to storage and automatic decryption when reading from storage. Doesn’t require changes on application code and queries.
- Fast encryption and decryption process using Oracle database caching optimization. Supports CPU-
based hardware acceleration on Intel AES- NI and SPARC T- series processors, including Oracle Exadata and Oracle Supercluster platforms. - Support for industry standard algorithms including:
- 3DES 168
- AES (128, 192, 256)
- Encrypts columns of a table.
- All encrypted columns of a table must use the same algorithm.
- Has options to undo encryption using decrypt clause in your alter table statement.
- Has options to change the encryption algorithm of all the encrypted columns of a table using rekey clause.
- Allows salting of encrypted column to produce a variance of encrypted result set for column data having identical information.
- B-
tree index is allowed on encrypted columns with No Salt.
- Supports all data types, all index types, and foreign keys.
- Encryption is done at the I/O level on a per-
block basis. - If there is a large number of columns in a table to be encrypted, tablespace encryption may provide better performance than column-
based encryption. - Encrypted tablespace are transportable as long as both the source and target platform had the same endian and the same wallet.
- Tablespace encryption does not require additional storage.
- By default, Data Pump exports are in plain text.
- Encryption of Data Pump files are based on the supplied password.
- Options for the scope of encryption:
- Encrypted columns only
- Data only
- Meta data only
- All
- Transparent Mode Encryption
- Uses the Oracle key management infrastructure. Requires the existence of an Oracle Wallet.
- No RMan code changes needed.
- Encryption and decryption of backups are transparent to the user.
- Password Mode Encryption
- Commonly used when backup are transported and restored to a target environment where a key infrastructure are non-
existent.
- Dual Mode Encryption
- Gives you the flexibility to either restore the backups using the keys or using the password.
- Useful when you create backups that are normally restored using Oracle Encryption Wallet but which occasionally would restore to an environment having no Oracle wallet.
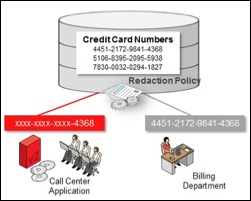
Oracle Data Redaction enables you to mask (redact) data that is returned from queries issued by applications.
Methods to redact column data:
- Full redaction. You redact all of the contents of the column data.
- Partial redaction. You redact a portion of the column data. For example, a Social Security number with asterisks (*), except for the last 4 digits.
- Regular expressions. You can use regular expressions to look for patterns of data to redact.
- Random redaction. The redacted data presented to the querying application user appears as randomly generated values each time it is displayed.
- The Data Redaction policy defines the following: What kind of redaction to perform, how the redaction should occur, and when the redaction takes place. Oracle Database performs the redaction at execution time, just before the data is displayed to the application user.
- A Data Redaction policy can be defined in such a way as to fully redact the values, partially redact the values, or randomly redact the values.
- A Data Redaction policy can be defined with a policy expression which allows for different application users to be presented with either redacted data or actual data, based on whether the policy expression returns TRUE or FALSE. Redaction takes place when the boolean result of evaluating the policy expression is TRUE. Policy expressions can make use of the SYS_SESSION_ROLES namespace with the SYS_CONTEXT function to check for enabled roles.
Benefits of Oracle Data Redaction
- You have different styles of redaction from which to choose.
- Because the data is redacted at runtime, Data Redaction is well suited to environments in which data is constantly changing.
- You can create the Data Redaction policies in one central location and easily manage them from there.
- The Data Redaction policies enable you to create a wide variety of function conditions based on SYS_CONTEXT values, which can be used at runtime to decide when the Data Redaction policies will apply to the results of the application user's query.
NETWORK COMMUNICATION ENCRYPTION
PCI Guideline: Encrypt network traffic for sensitive data
- For web server, use HTTPS protocol
- Use HTTPS protocol to encrypt sensitive data passed between client and server.
- Requires signed digital certificate to enable SSL.
- For Oracle Net Services, use SSL or native encryption.
- Uses Oracle Advanced Security to encrypt network connections between databases, application servers, and client computers.
- SSL
- Uses TCPS protocol for TCP/IP with SSL.
- Requires Oracle Wallet installed on both database and client servers to manage the digital certificates issued by the Certificate Authority.
- Digital certificates are used to encrypt the connection between the client and the server, and it is also used to authenticate a client.
- Requires wallet configuration at the sqlnet.ora
- Ideal for use on server-
to- server communication such as an application server connection to a database server or a database- to- database connection through dblink.
- End-
to- end native encryption
- Uses Net manager to configure advanced security for network encryption.
- Requires configuration of SQLNET encryption parameters to set:
- Encryption type (AES, 3DES, RC4, etc.)
- Matching encryption seed
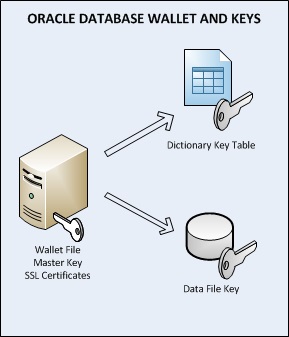
A wallet is a password-
- The Master Key is stored in a PKCS12 wallet or a PKCS11-
based Hardware Security Module (SafeNET, nCipher). - TDE creates a Key for each table that uses encrypted columns and each encrypted tablespace.
- Table keys are stored in the database’ data dictionary and the tablespace keys are stored in the tablespace data files.
- Both the tablespace and table keys are encrypted by the Master Key.
- Two tier architecture: The Master Key and Table Key can be re-
keyed independently. - Manages keys automatically.
- Re-
keying the Master Key does not cause the encrypted columns to be re- encrypted thus minimizing the impact on the database. - Maintains a history of past Master Keys for recovery of old data or if the database is recovered to a point-
in- time before the regeneration of master key. - Oracle Wallet backup can be done through the regular OS backup.