

©2015 -



Information Technology



Oracle Advanced Security -
IV. EXPORT CERT SIGNING REQUEST
The cert signing request (CSR) can be exported to a file for which you would send this to the certificate authority for a signed cert.
You do this to both the Server and the Client OWM (Oracle Wallet Manager).
Expand the Wallet folder and select the appropriate Certificate Request.
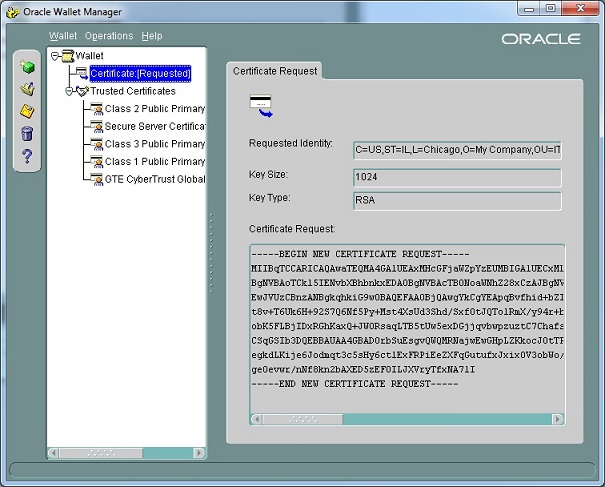
At the Operations menu, select Export Certificate Request
Enter your export file name. In my case, the filename is db_cert_request.csr for the server and client_cert_request.csr for the client.
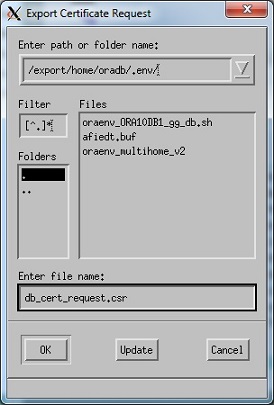
Now, Save the wallet and Exit.
At this point, we now have to submit the generated CSR files of both the db server and the client to the Certificate Authority for signing.
Since this is just a lab exercise, I won’t be submitting my cert request to the Certificate Authority vendors (Thawte, Verisign, Go Daddy, etc.) where it charges me for a fee. Instead, I will use the open source SSL.CA created by Yeak Nai Siew as my CA for certificate signing. Apparently his program is no longer available at the openssl.org. I found lately that his second version is available at GitHub but I haven’t tested that version yet since in my demo below I am using his first original version. From what I understand, the second version only has an additional functionality to allow renewal of certs. Other than that, the core program is the same as the first version. Keep in mind that for production implementation you’ve got to use the real Certificate Authority.
NOTE: ssl.ca application is primarily coded for Solaris Unix. But the author claims that it will also work on Linux. To validate this claim, my installation below is done on a Linux 2.6.32 platform. And it works perfectly!
As root,
cp ssl.ca-
cd /usr/local
[root@pacificnfs local]# tar xvf ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
ssl.ca-
[root@pacificnfs local]# chown -
At this point, I have installed the ssl.ca at /usr/local/ssl.ca-
Generate PRIVATE KEY for Root Trusted Cert
The ca.key pass phrase is the one used for generating the root cert. The longer and complex the phrase, the better. We will use openssl to generate the key. The openssl application is mostly included in Linux distributions, so no need to install this tool.
My ca.key pass phrase: Oracl3_Advanc3d_S3cur!ty
[root@pacificnfs local]# which openssl
/usr/bin/openssl
[root@pacificnfs ssl.ca-
[root@pacificnfs ssl.ca-
Generating RSA private key, 1024 bit long modulus
.......++++++
.++++++
e is 65537 (0x10001)
Enter pass phrase for ca.key:
Verifying -
[root@pacificnfs ssl.ca-
[root@pacificnfs ssl.ca-
total 68
-
-
-
-
-
-
-
-
-
-
-
[root@pacificnfs ssl.ca-
Generate TRUSTED ROOT CERTIFICATE
Now that we have the key, we can now create the root cert which simulates our CA identity.
[root@pacificnfs ssl.ca-
Self-
Enter pass phrase for ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-
Country Name (2 letter code) [MY]:US
State or Province Name (full name) [Perak]:Illinois
Locality Name (eg, city) [Sitiawan]:Chicago
Organization Name (eg, company) [My Directory Sdn Bhd]:My Cert Authority
Organizational Unit Name (eg, section) [Certification Services Division]:Cert Services Division
Common Name (eg, MD Root CA) []:My Root CA
Email Address []:admin@pacificnfs.com
[root@pacificnfs ssl.ca-
total 108
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
drwxr-
-
[root@pacificnfs ssl.ca-
Now that we have the ca.key and the Root Trusted Cert, let’s sign the CSR of the database and the client.
I have to upload the csr files onto the server where I installed the ssl.ca before I proceed with the next steps.
Signed Cert For Database
[root@pacificnfs ssl.ca-
CA signing: db_cert_request.csr -
Using configuration from ca.config
Enter pass phrase for ./ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :PRINTABLE:'pacific'
organizationalUnitName:PRINTABLE:'IT Database'
organizationName :PRINTABLE:'My Company'
localityName :PRINTABLE:'Chicago'
stateOrProvinceName :PRINTABLE:'IL'
countryName :PRINTABLE:'US'
Certificate is to be certified until Nov 14 19:24:27 2015 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: db_cert_request.crt <-
db_cert_request.crt: OK
[root@pacificnfs ssl.ca-
[root@pacificnfs ssl.ca-
-
-
[root@pacificnfs ssl.ca-
Signed Cert For the Client Application
[root@pacificnfs ssl.ca-
CA signing: client_cert_request.csr -
Using configuration from ca.config
Enter pass phrase for ./ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :PRINTABLE:'pacificnfs'
organizationalUnitName:PRINTABLE:'IT Application'
organizationName :PRINTABLE:'MyCompany'
localityName :PRINTABLE:'Chicago'
stateOrProvinceName :PRINTABLE:'IL'
countryName :PRINTABLE:'US'
Certificate is to be certified until Nov 11 23:59:54 2015 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: client_cert_request.crt <-
client_cert_request.crt: OK
[root@pacificnfs ssl.ca-
At this point, we now have two signed certificates -